This entry was posted in General Security, Research, Wordfence, WordPress Security on January 27, 2021 by Ram Gall4 Replies
- Wordfence is a popular security plugin that you can use to protect your WordPress site from a wide range of cyberattacks. One of which is brute force attacks. A brute force attack is a cyberattack type where an attacker randomly enters many passwords with the purpose of eventually guessing the correct one.
- To install Wordfence Login Security on WordPress Multisite installations: Install Wordfence Login Security via the plugin directory or by uploading the ZIP file. Network Activate Wordfence Login Security. This step is important because until you network activate it, your sites will see the plugin option on their ‘Plugins’ menu.
- It lets Wordfence run prior to WordPress core, themes and plugins, which results in improved protection against more advanced security threats. Follow the steps below to setup the extended protection firewall: Go to Wordfence Firewall in your WordPress dashboard’s left sidebar. Once there, click the Optimize the Wordfence Firewall button.
Over the course of 2020, and in the process of protecting over 4 million WordPress customers, the Wordfence Threat Intelligence team gathered a massive amount of raw data from attacks targeting WordPress and infection trends, in addition to the malware samples gathered by our Site Cleaning team. Attacks on WordPress can be categorized in three major categories, with malicious login attempts and vulnerability exploit attacks predictably leading the way. In a surprising trend, nulled plugin malware also staked its claim as a prominent intrusion vector.
A common question WordPress users ask is how to handle website security, especially when the business starts to expand. If you already have kudos to give to basic Wordfence — the highly-rated security plugin for WordPress — then this Wordfence review will help you separate the wheat from the chaff about its essential premium aspects. WordPress Security Scanner. As the name suggests, a WordPress scanner from WordFence scans core website files, plugins, and themes for malware, backdoors, spam, code injections, and bad URLs. It also confirms your files’ integrity by comparing them with files in the WordPress.org repository.
In this report, we provide an overview of the primary threats targeting the WordPress ecosystem as well as recommendations for effective mitigation.
90 Billion Malicious WordPress Login Attempts
Over the course of 2020, Wordfence blocked more than 90 billion malicious login attempts from over 57 million unique IP addresses, at a rate of 2,800 attacks per second targeting WordPress.
Malicious login attempts were by far the most common attack vector targeting WordPress sites. These attempts included credential stuffing attacks using lists of stolen credentials, dictionary attacks, and traditional brute-force attacks.
Key Takeaway: Use Multi-Factor Authentication to Protect WordPress
While the vast majority of malicious login attempts targeting WordPress are destined to be unsuccessful, it only takes a single successful login to compromise a WordPress site. The brute-force mitigation provided by Wordfence is very effective, and using multi-factor authentication adds another layer of protection to WordPress logins.
Multi-factor authentication can completely prevent attackers from gaining access to a site via automated login attempts. This holds true even in unfortunate cases where user accounts on a WordPress site are reusing credentials that have been exposed in a data breach and haven’t yet been updated.
Wordfence offers free login security options within the full featured Wordfence Security plugin. We also offer free login security, including multi-factor authentication, via the standalone Wordfence Login Security plugin.
4.3 Billion Vulnerability Exploit Attempts Targeting WordPress
Wordfence blocked 4.3 billion attempts to exploit vulnerabilities from over 9.7 million unique IP addresses in 2020. Here were the five most common attacks over the course of the year:
- Directory Traversal attacks, including relative and absolute paths, made up 43% of all vulnerability exploit attempts, at 1.8 billion attacks. While the majority of these were attempts to gain access to sensitive data contained in site wp-config.php files, many were also attempts at local file inclusion (LFI).
- SQL Injection was the second most commonly attacked category of vulnerabilities at 21% of all attempts with 909.4 million attacks.
- Malicious file uploads intended to achieve Remote Code Execution(RCE) were the third most commonly attacked category of vulnerabilities at 11% of all attempts with 454.8 million attacks.
- Cross-Site Scripting(XSS) was the fourth most commonly attacked category of vulnerabilities at 8% of all attempts with 330 million attacks.
- Authentication Bypass vulnerabilities were the fifth most commonly attacked category of flaws at 3% of all attempts with 140.8 million attacks.
Key Takeaway: Use a WAF to Protect Your WordPress Site
A Web Application Firewall, such the Wordfence WAF, is absolutely critical to keeping your WordPress site secure. Nearly every one of the 4 million sites in our network experienced at least one of each of these attacks over the course of 2020.
Wordfence is the leading WordPress firewall solution and is continually updated to protect against existing and emerging WordPress attacks. In 2020, we deployed 108 new rules to the Wordfence firewall to protect our customers from unique exploits.
Wordfence Premium customers also benefit from our IP blocklist which is extremely effective at blocking known bad actors. While the Wordfence Premium blocklist generally consists of 15,000 to 40,000 unique IP addresses at any given time, the list is continually updated as new attackers emerge and as infected servers are cleaned. For the entire year, the Wordfence Premium blocklist prevented 2.55 billion attacks from 628,564 unique IP addresses, each of which spent some time on our blocklist in 2020.
Malware From Nulled Plugins and Themes Is the Most Widespread Threat to WordPress Security
The Wordfence scanner detected more than 70 million malicious files on 1.2 million WordPress sites in the past year. The vast majority of these sites were cleaned by the end of the year. Only 132,000 sites infected at the beginning of 2020 were still infected by the end of the year, many of them likely abandoned.
The WP-VCD malware was the single most common malware threat to WordPress, counting for 154,928 or 13% of all infected sites in 2020. Overall, the Wordfence scanner found malware originating from a nulled plugin or theme on 206,000 sites, accounting for over 17% of all infected sites. Nulled plugins and themes are pirated copies of premium plugins and themes with their license checking features disabled or removed, which typically contain backdoor functionality.
Other obfuscated PHP backdoors made up the remainder of the top 5 most widely detected threats.
Key Takeaway: Educate Yourself and Your Organization About WordPress Security
Policy controls are just as important as technical controls, because insider threats capable of bypassing technical controls can cause immense damage to an organization. This applies to a WordPress site just as much as it does to a Fortune 500 company.
While insider threats are often portrayed as malicious, the vast majority of them are accidental, from clicking a phishing link to installing nulled plugins. Much like phishing links, nulled plugins are specifically designed to take advantage of naive insiders.
The best way to avoid making this kind of mistake is to educate yourself and everyone else in your organization. While a plugin like Wordfence can detect malware originating from a nulled plugin or theme after it has been installed, only proper training can prevent a misguided administrator from accidentally installing it in the first place.
Conclusion
In our review, we identified the three most widespread threats faced by WordPress sites in 2020: malicious login attempts, attempts to exploit vulnerabilities, and malware originating from nulled plugins and themes.
We also explored key takeaways from these threats and how to most effectively mitigate them. While technical controls such as Wordfence can dramatically improve your WordPress site security posture, the human element is always the weakest link in any organization. Education is the best way to make sure your site is secure.
As such, Wordfence is committed to educating the WordPress community about security via the official Wordfence blog, our Think Like a Hacker Podcast, and Wordfence Live which is broadcast every Tuesday, in addition to our presence at many WordPress events. Our Threat Intelligence team works hard to protect every one of our users, and it’s all thanks to the support of our Premium Customers, who make it possible for us to help keep WordPress safe.
This article has been updated to provide further information about Nulled plugins and themes
Wordfence is a free security plugin for WordPress. Security “plugins” for WordPress are often highly criticized as many may give a false sense of security or simply just automate creating .htaccess files – sometimes recklessly. However, Wordfence stands clear apart and above other plugins as it offers malware detection, checks for out-of-date plugins or themes, provides firewall throttling or blocking rules, has the ability to restore compromised or altered WordPress theme or plugin files, and offers an optional paid vulnerability scan from their data center. Those are just a few of the highlights which are to be touched upon below. Let’s dive in.
The Wordfence Scan
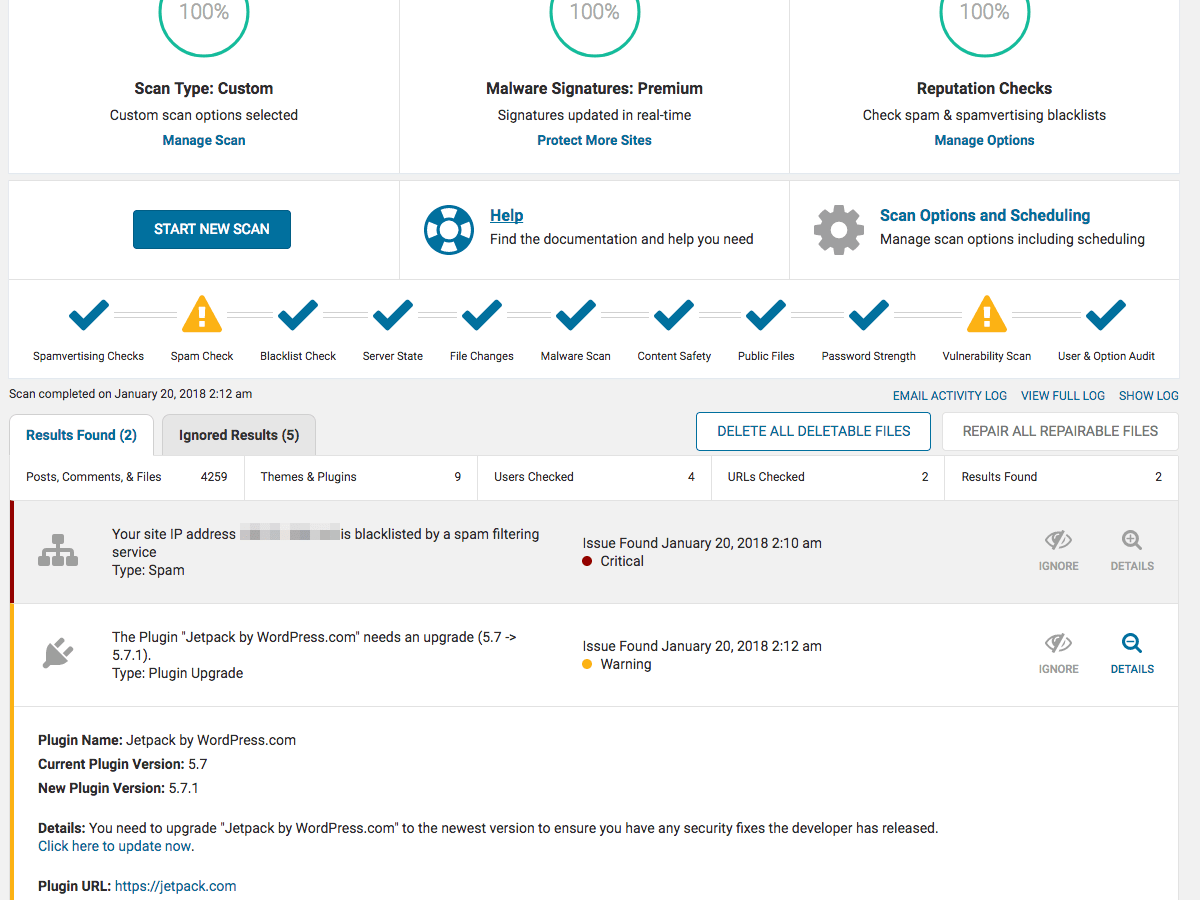
Wordfence functionality is based around a security scan the plugin performs. Out of the box, the plugin is ready to use and scan. Simply install and click Scan. The Wordfence Scan checks for the following issues:
Remote scan of public facing site [paid feature]
Comparing core WordPress files against originals in repository
Comparing open source themes against WordPress.org originals
Comparing plugins against WordPress.org originals
Scanning for known malware files
Scanning file contents for infections and vulnerabilities
Scanning files for URLs in Google’s Safe Browsing List
Scanning posts for URL’s in Google’s Safe Browsing List
Scanning comments for URL’s in Google’s Safe Browsing List
Scanning for weak passwords
Scanning DNS for unauthorized changes
Scanning to check available disk space
Scanning for old themes, plugins and core files
Restore Modified or Possibly Compromised Plugin or Theme Files
The biggest feature of Wordfence is that it analyzes all core WordPress files, theme files, and plugin files for changes against the current available versions of those components. Users can click to repair/restore the original version of the file, view changes on screen, or ignore the finding. To avoid a customized theme from being flagged in this check, one should make use of WordPress child themes for theme changes.
Wordfence performs this by checking MD5 and SHA hashes of the installed files in a WordPress installation against a database of hashes of original files. The hashes are sent securely via 443 SSL to the Wordfence servers. This provides a quick and simple way to compare if files are different or have been modified for any reason, such as from malware or compromise.
Live Traffic
Wordfence offers an optional Live Traffic view. This runs via JavaScript that records its own analytics separate from any other logging. Information such as browser agent, IP address, geo-location, and the ability to click ‘block’ beside the IP makes this an invaluable feature. The only feature lacking is any ability to dump or export all of the traffic data to a CSV or XML file, which would be valuable.
Blocked IPs
Antoher feature in Wordfence is the ability to block an IP address from access to the WordPress site. Specific IP addresses can also be blocked from accessing the WordPress Login page to add security around the login area.
Note that Firewall and IP Blocking only prevent access to the WordPress site itself. This is not a replacement for a full operating system firewall, nor does it interact with iptables or other operating system level restrictions. Frankly, a WordPress plugin controlling an operating system firewall would probably be a bad idea. An example screen that is shown to a blocked IP is below.
Wordfence Wordpress Plugin
Country Blocking
Scheduled Scanning
Two paid features are blocking entire geographical regions by geo-location as well as scheduled scanning. These add convenience but are not required for the full plugin functionality.
Wordfence Options
Once single Options page provides the entire configuration for Wordfence. Making changes here is completely optional, though users who want to make more changes under the hood will want to inspect this area.
Starting at the top, a drop down menu offers a quick security-hardening setting. In case the site is under attack or being the focus of abuse, the security level can be changed quickly here to various levels. Otherwise, each individual option can be set as shown below.
Advanced Options
Alerts
Various email alerts are possible from email alert when a user logs into the site, to emails about critical security problems found. Macos catalina download for pc.
Live Traffic View
Here the Live Traffic View can be disabled if desired. I mention this as the only information leakage from the Wordfence plugin is the Live Traffic View javascript which is visible in the HTML source. (See screenshot below). It is still possible to block IP addresses with Live Traffic View disabled, though of course no fancy Live Traffic View would be available to see live traffic.
Scans to Include
In the Scans to Include section, it is best to enable two options that are not on by default to scan themes and plugins for changes. Often malware or another compromise will alter or change files on the server. These options let Wordfence check that all files in themes and plugins are of their originals and not compromised.
– Scan theme files against repository versions for changes
– Scan plugin files against repository versions for changes
Firewall Rules
Wordfence offers its own firewall to either throttle or block IP addresses based on various actions.
For instance, to avoid situations where the site may be flooded or DoS’d, enable the feature to throttle or block a connection after a large number of requests (32 per second). As previously mentioned, these rules only restrict access to the WordPress site itself, and have no effect on the operating system level Firewall.
Login Security Options
To add additional security around the WordPress login, Wordfence offers many good features. After X number of bad login attempts, the IP can be blocked. The more fascinating feature offered here is Don’t let WordPress reveal valid users in login errors. Many WordPress hacks based around the login page are from information leakage where WordPress confirms valid usernames at the login page.
While these are great features to add security around the login, the best security is to prevent access to the WordPress login page entirely by Apache server authentication if at all possible.
Other Options
In the final section Other Options, specify a home or work IP address in the whitelist so Wordfence does not block or limit valid connections from valid WordPress administrators.
If the option to Participate in the Wordfence Security Network is selected, IP addresses that have violated login or firewall rules are sent to Wordfence to help in a global block list for other users. If desired, disable this option for privacy reasons.
Effectiveness and Conclusions
Wordfence Wordpress Exploit
Wordfence offers extremely easy deployment of added security layers to WordPress. The highly customized options make Wordfence a good choice for one who perhaps is not interested in the Firewall, but only want to audit code changes. The Firewall can be disabled, and only code changes can be scanned, as one example. Wordfence has a large user community on their forums ( http://www.wordfence.com/forums ) and offers support for paid users. A negative often spoken of security plugins is that they often only automate or change what one could change for themselves anyway. But here Wordfence’s code auditing, firewall with throttling options, malware detection, and other features are a bit far from what one could do themselves or at least not without quite a bit of effort. Wordfence operates in large part with its cloud servers located in Seattle, Washington who play a large part in the code auditing and IP block lists correlation, as well as perform scanning for paid users.
Wordfence Wordpress Plugin
Of all of the various security plugins for WordPress, Wordfence provides unique layered security options with an extremely easy-to-use interface. Check it out at http://www.wordfence.com.
